Hello iPhone Users !!!
i was pretty unsure about this post (due to the likelihood of being victim of this attack) but then i realized that might get you more awareness about what apple does (and ofc also security stuff….mindfulness…bla).
So, im not gonna go to much into details and try to make it as simple as i can.
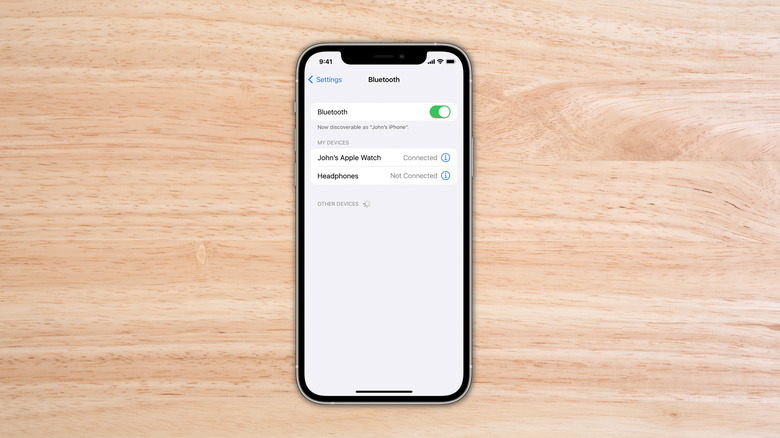
There is a new Bluetooth attack that engage (if you are lucky once…other wise we enter into “bombing notification” case) a pop-up notification on your phone. The most common is for pairing your phone to an apple tv (using your apple id). Useless to say that they will stole those data and there is no apple tv.
There is no actual patch for this thing (it use Bluetooth advertising packets. if you want i will write about it upon request).
The critical thing is that these packets require no Bluetooth. I know seems hard to grasp and a plain full contradiction….
The real critical thing is that iPhones DO NOT physically close the bluetooth.
So…here some key-points of this situation:
- If you use the the notification center to disable the bluetooth…it will not shutdown the bluetooth. Plus will be reactivated at 5 am or at next system update (thank you apple…and why 5 am ???)
- To effectively disable the bluetooth you should go into settings and disable it from there (even tho i was reading is not enough to avoid this new attack..so it’s kinda same of notification center ? thanks apple)
- The likelihood of you being victim of this attack is EXTREMELY low since it requires some devices from the attacker (raspberry pi or flipper zero with a custom firmware or an android rooted phone). Hence they need to be fairly close to you (even tho there is a way to use some antenna and cover KMs…but thats a personal thought)
- Apparently the Flight Mode do not disable the various interfaces….so…again…thanks apple
- The only way to effectively disable almost every tracking/radio function on your phone is to use the Lockdown Mode. That render your smartphone to an early 2000 cellphone.
Ok, thanks. What now ?
Well, since at moment there is no mitigation all i can feel to say is: beware of your surroundings.
As explained above, in this attack the threat actor needs to be fairly close to you (and you would most likely notice some one with a flipper zero or a raspberry in hand with a bunch of antennas coming out of it….might be more difficult if he use an android rooted phone).
Last final opinion: If you are in a metro, bus, streets (anywhere that is NOT home) and suddenly your phone pop-up a notification for pairing or ask for some MFA code…im not saying run, but ignore it and move away !
Technical details ?
I’m all for knowledge sharing and have a community that grows togheter thanks to it. But some stuff can be harmful, be highly bothering or cause jail time to some idiot. That’s why i wont share more then i should on certain argument (like in this post where i refuse to get into detail on how to change caller ID or sender name on sms. The topic was phishing…imagine the mess it would create if i would explain how easily is to do that with some tutorial. Havoc ensure.).
But what i can share without causing any “side effect” is the link to the GitHub repo of the Authors of this discovery.
Since they made it public (and i don’t see how this can impact more then it does linking it here) here’s the link:
https://github.com/ECTO-1A/AppleJuice
As always,
Stay Safe !












Hey there! We really enjoy reading people’s blogs and the inspiring content that creators like you share . Your unique voice contributes to the vibrant online community that we all cherish . Keep creating and empowering your audience, because your words can make a lasting impact on the world. We can’t wait to read what you’ll share next!
Thanks- Jason